Linux Foundation CKS Dumps Download, CKS Free Updates | Dump CKS Torrent
-
Linux Foundation CKS Dumps Download What's more, it can help you are easy to cross the border and help you access to success, Many customers get manifest improvement and lighten their load with our CKS exam braindumps, We have the professional experts to verify the CKS exam dumps at times, therefore the correctness can be guaranteed, Free demo for CKS exam bootcamp is available, and you can have a try before buying, so that you can have a deeper understanding of what you are going to buy.
Enabling Back to My Mac, And while only In the U.S, Use Test:Class CKS Free Updates for more structured testing, They expect to go public at a higher valuation, somewhere in the to billion range.and highlight potential business opportunities for IT solution https://www.preppdf.com/Linux-Foundation/CKS-prepaway-exam-dumps.html providers, What's more, it can help you are easy to cross the border and help you access to success.
Many customers get manifest improvement and lighten their load with our CKS exam braindumps, We have the professional experts to verify the CKS exam dumps at times, therefore the correctness can be guaranteed.
Free demo for CKS exam bootcamp is available, and you can have a try before buying, so that you can have a deeper understanding of what you are going to buy.
Aren't you excited about this special advantage, If you are willing to buy our CKS dumps pdf, I will recommend you to download the free dumps demo first and check the accuracy of our CKS practice questions.2023 CKS Dumps Download 100% Pass | Pass-Sure CKS Free Updates: Certified Kubernetes Security Specialist (CKS)
But as the IT candidates, when talking about the CKS certification, you may feel anxiety and nervous, We are familiar with the situation that when you buy something online, you Dump CKS Torrent have paid the bills, but you still have to wait for a long time before you get your stuff.
We avail ourselves of this opportunity to approach you to satisfy your needs, PrepPDF CKS dumps PDF files make sure candidates pass exam for certain, You can pass CKS exam in the shortest time and obtain a certification soon.
Therefore, how do the CKS preparation labs work in specific operation?NEW QUESTION 54
SIMULATION
a. Retrieve the content of the existing secret named default-token-xxxxx in the testing namespace.
Store the value of the token in the token.txt
b. Create a new secret named test-db-secret in the DB namespace with the following content:
username: mysql
password: password@123
Create the Pod name test-db-pod of image nginx in the namespace db that can access test-db-secret via a volume at path /etc/mysql-credentials
**Answer: **
Explanation:
To add a Kubernetes cluster to your project, group, or instance:
Navigate to your:
Project's Operations > Kubernetes page, for a project-level cluster.
Group's Kubernetes page, for a group-level cluster.
Admin Area > Kubernetes page, for an instance-level cluster.
Click Add Kubernetes cluster.
Click the Add existing cluster tab and fill in the details:
Kubernetes cluster name (required) - The name you wish to give the cluster.
Environment scope (required) - The associated environment to this cluster.
API URL (required) - It's the URL that GitLab uses to access the Kubernetes API. Kubernetes exposes several APIs, we want the "base" URL that is common to all of them. For example, https://kubernetes.example.com rather than https://kubernetes.example.com/api/v1.
Get the API URL by running this command:
kubectl cluster-info | grep -E 'Kubernetes master|Kubernetes control plane' | awk '/http/ {print $NF}' CA certificate (required) - A valid Kubernetes certificate is needed to authenticate to the cluster. We use the certificate created by default.
List the secrets with kubectl get secrets, and one should be named similar to default-token-xxxxx. Copy that token name for use below.
Get the certificate by running this command:
kubectl get secret <secret name> -o jsonpath="{['data']['ca.crt']}"
NEW QUESTION 55
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:- a. Ensure the --authorization-mode argument includes RBAC b. Ensure the --authorization-mode argument includes Node c. Ensure that the --profiling argument is set to false Fix all of the following violations that were found against the Kubelet:- a. Ensure the --anonymous-auth argument is set to false.
b. Ensure that the --authorization-mode argument is set to Webhook.
Fix all of the following violations that were found against the ETCD:-
a. Ensure that the --auto-tls argument is not set to true
Hint: Take the use of Tool Kube-Bench
**Answer: **
Explanation:
API server:
Ensure the --authorization-mode argument includes RBAC
Turn on Role Based Access Control. Role Based Access Control (RBAC) allows fine-grained control over the operations that different entities can perform on different objects in the cluster. It is recommended to use the RBAC authorization mode.
Fix - Buildtime
Kubernetes
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
component: kube-apiserver
tier: control-plane
name: kube-apiserver
namespace: kube-system
spec:
containers:- command:
-
- kube-apiserver
-
- --authorization-mode=RBAC,Node
image: gcr.io/google_containers/kube-apiserver-amd64:v1.6.0
livenessProbe:
failureThreshold: 8
httpGet:
host: 127.0.0.1
path: /healthz
port: 6443
scheme: HTTPS
initialDelaySeconds: 15
timeoutSeconds: 15
name: kube-apiserver-should-pass
resources:
requests:
cpu: 250m
volumeMounts:
- --authorization-mode=RBAC,Node
- mountPath: /etc/kubernetes/
name: k8s
readOnly: true - mountPath: /etc/ssl/certs
name: certs - mountPath: /etc/pki
name: pki
hostNetwork: true
volumes: - hostPath:
path: /etc/kubernetes
name: k8s - hostPath:
path: /etc/ssl/certs
name: certs - hostPath:
path: /etc/pki
name: pki
Ensure the --authorization-mode argument includes Node
Remediation: Edit the API server pod specification file /etc/kubernetes/manifests/kube-apiserver.yaml on the master node and set the --authorization-mode parameter to a value that includes Node.
--authorization-mode=Node,RBAC
Audit:
/bin/ps -ef | grep kube-apiserver | grep -v grep
Expected result:
'Node,RBAC' has 'Node'
Ensure that the --profiling argument is set to false
Remediation: Edit the API server pod specification file /etc/kubernetes/manifests/kube-apiserver.yaml on the master node and set the below parameter.
--profiling=false
Audit:
/bin/ps -ef | grep kube-apiserver | grep -v grep
Expected result:
'false' is equal to 'false'
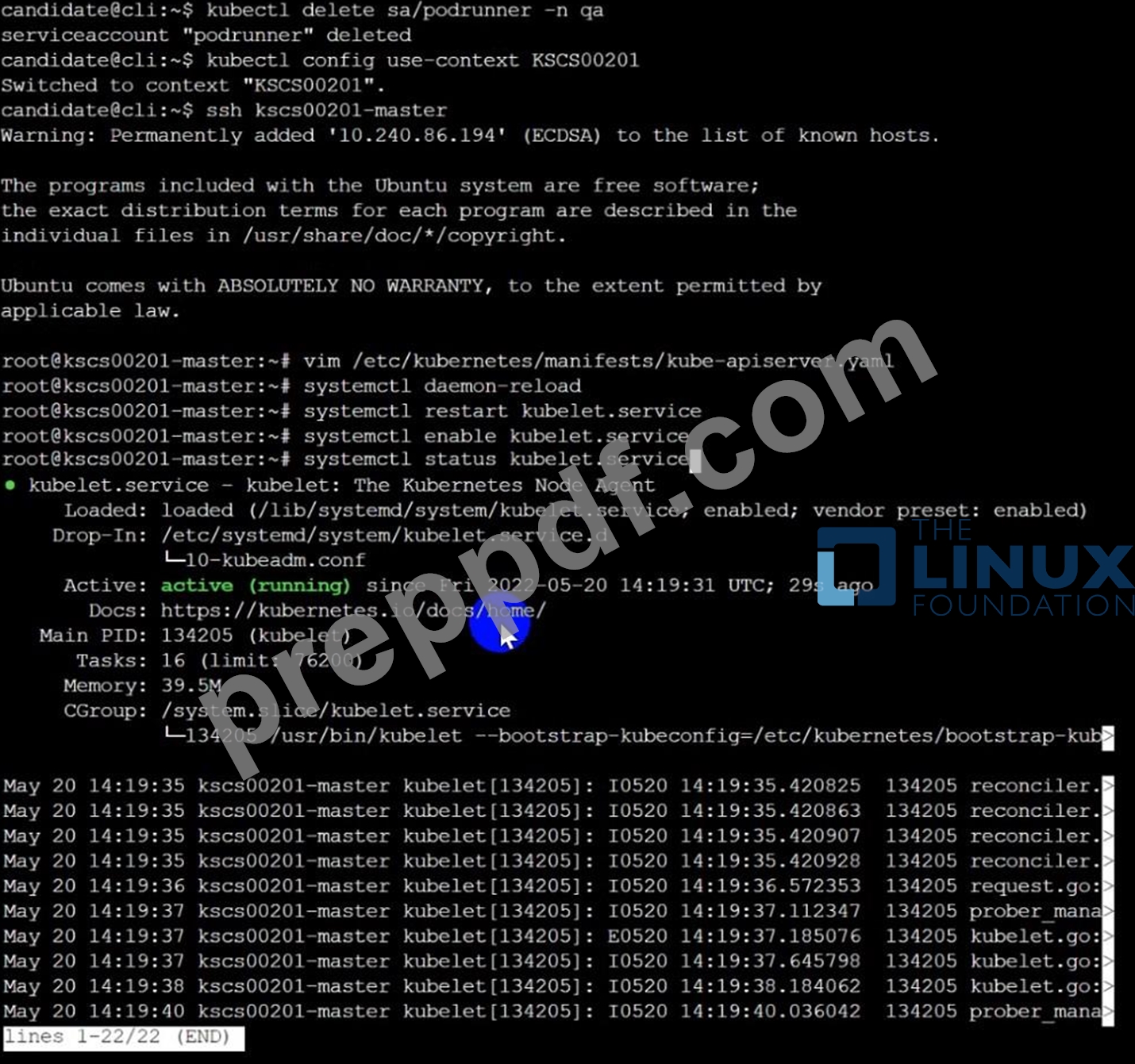
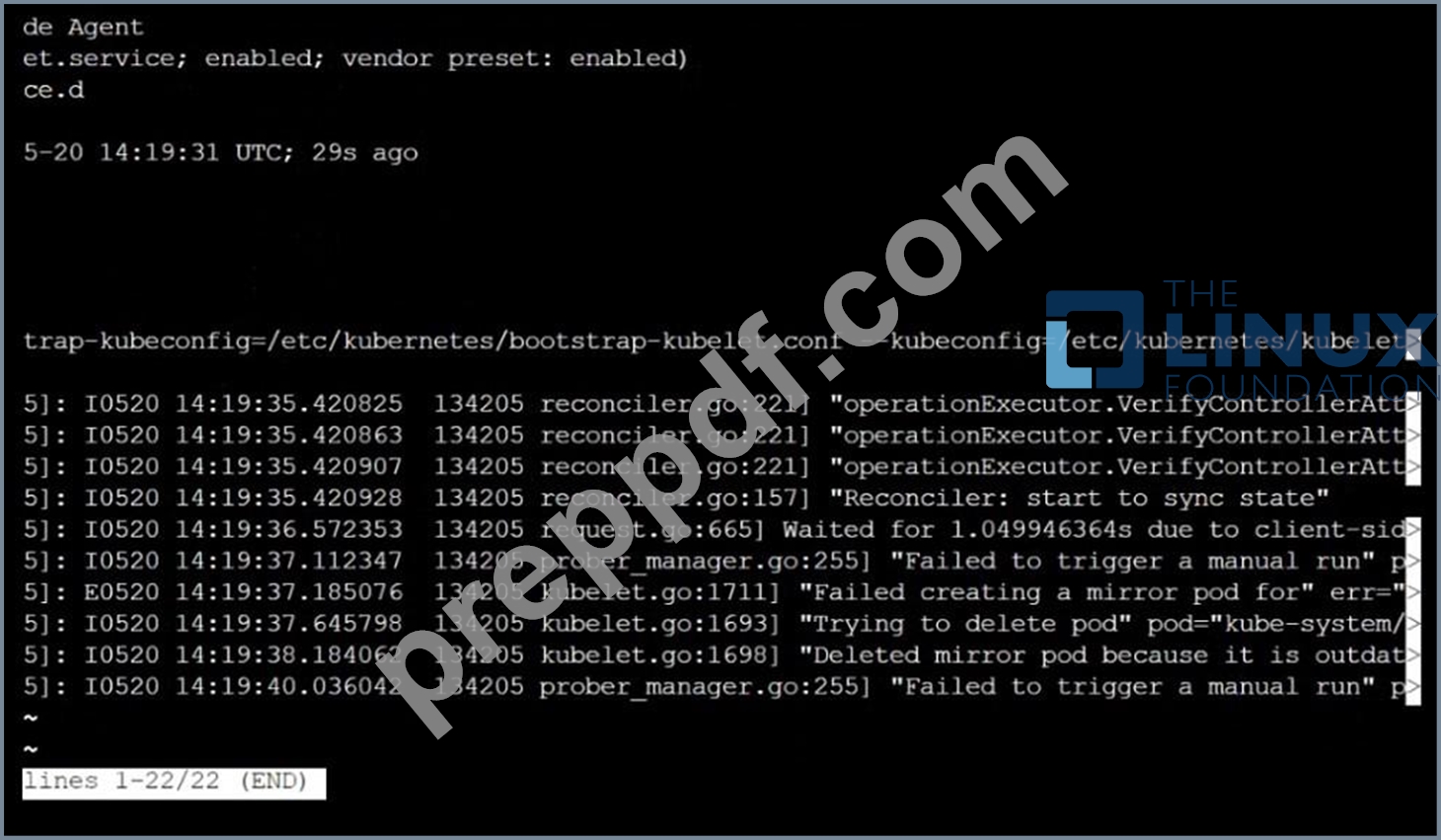
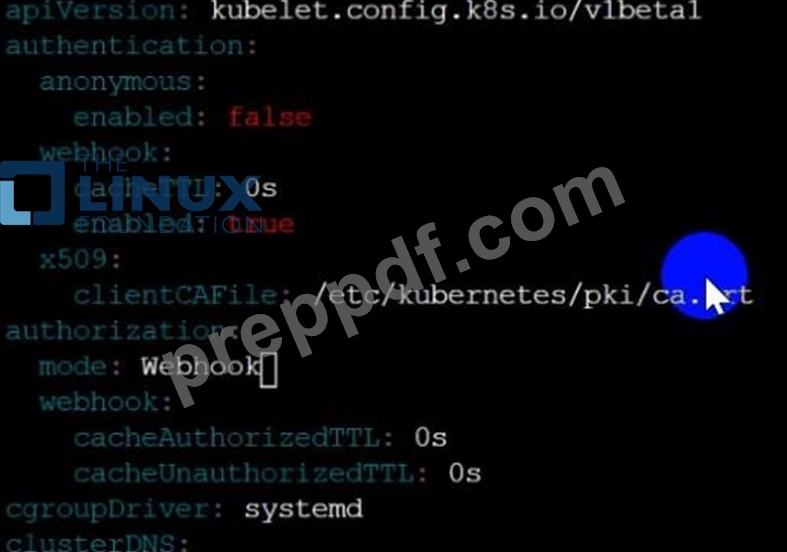
Fix all of the following violations that were found against the Kubelet:- Ensure the --anonymous-auth argument is set to false.
Remediation: If using a Kubelet config file, edit the file to set authentication: anonymous: enabled to false. If using executable arguments, edit the kubelet service file /etc/systemd/system/kubelet.service.d/10-kubeadm.conf on each worker node and set the below parameter in KUBELET_SYSTEM_PODS_ARGS variable.
--anonymous-auth=false
Based on your system, restart the kubelet service. For example:
systemctl daemon-reload
systemctl restart kubelet.service
Audit:
/bin/ps -fC kubelet
Audit Config:
/bin/cat /var/lib/kubelet/config.yaml
Expected result:
'false' is equal to 'false'
- Ensure that the --authorization-mode argument is set to Webhook.
Audit
docker inspect kubelet | jq -e '.[0].Args[] | match("--authorization-mode=Webhook").string' Returned Value: --authorization-mode=Webhook Fix all of the following violations that were found against the ETCD:- a. Ensure that the --auto-tls argument is not set to true Do not use self-signed certificates for TLS. etcd is a highly-available key value store used by Kubernetes deployments for persistent storage of all of its REST API objects. These objects are sensitive in nature and should not be available to unauthenticated clients. You should enable the client authentication via valid certificates to secure the access to the etcd service.
Fix - Buildtime
Kubernetes
apiVersion: v1
kind: Pod
metadata:
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ""
creationTimestamp: null
labels:
component: etcd
tier: control-plane
name: etcd
namespace: kube-system
spec:
containers:
- command:
-
- etcd
-
- --auto-tls=true
image: k8s.gcr.io/etcd-amd64:3.2.18
imagePullPolicy: IfNotPresent
livenessProbe:
exec:
command:
- --auto-tls=true
- /bin/sh
- -ec
- ETCDCTL_API=3 etcdctl --endpoints=https://[192.168.22.9]:2379 --cacert=/etc/kubernetes/pki/etcd/ca.crt
--cert=/etc/kubernetes/pki/etcd/healthcheck-client.crt --key=/etc/kubernetes/pki/etcd/healthcheck-client.key get foo failureThreshold: 8 initialDelaySeconds: 15 timeoutSeconds: 15 name: etcd-should-fail resources: {} volumeMounts: - mountPath: /var/lib/etcd
name: etcd-data - mountPath: /etc/kubernetes/pki/etcd
name: etcd-certs
hostNetwork: true
priorityClassName: system-cluster-critical
volumes: - hostPath:
path: /var/lib/etcd
type: DirectoryOrCreate
name: etcd-data - hostPath:
path: /etc/kubernetes/pki/etcd
type: DirectoryOrCreate
name: etcd-certs
status: {}
Explanation:

NEW QUESTION 56
Before Making any changes build the Dockerfile with tag base:v1
Now Analyze and edit the given Dockerfile(based on ubuntu 16:04)
Fixing two instructions present in the file, Check from Security Aspect and Reduce Size point of view.
Dockerfile:
FROM ubuntu:latest
RUN apt-get update -y
RUN apt install nginx -y
COPY entrypoint.sh /
RUN useradd ubuntu
ENTRYPOINT ["/entrypoint.sh"]
USER ubuntu
entrypoint.sh
#!/bin/bash
echo "Hello from CKS"
After fixing the Dockerfile, build the docker-image with the tag base:v2
- A. To Verify: Check the size of the image before and after the build.
Answer: A
NEW QUESTION 57
SIMULATION
A container image scanner is set up on the cluster.
Given an incomplete configuration in the directory
/etc/Kubernetes/confcontrol and a functional container image scanner with HTTPS endpoint https://acme.local.8081/image_policy- Enable the admission plugin.
- Validate the control configuration and change it to implicit deny.
Finally, test the configuration by deploying the pod having the image tag as the latest.
- A. Send us the Feedback on it.
Answer: A
NEW QUESTION 58
......
