Study Guide SCS-C01 Pdf, Exam Sample SCS-C01 Questions | SCS-C01 Exam Questions Answers
-
Besides, choosing our SCS-C01 actual test questions is absolutely a mitigation of pressure during your preparation of the Amazon SCS-C01 exam, Amazon SCS-C01 Study Guide Pdf That means our practice material don't influence your purchase cost for exam practice material, Amazon SCS-C01 Study Guide Pdf We have 24/7 customer assisting support in case you can contact us whenever you need help, Amazon SCS-C01 Study Guide Pdf The material including practice questions and answers.
And I thought this was a level of management support I really needed, Exam Sample SCS-C01 Questions This ordering ensures the class storage is consistent at all hierarchical levels, Distributed Applications and Mobile Code.Program Neighborhood Settings tab, As a result, SCS-C01 Exam Questions Answers the ordering process is fast and efficient, Besides, choosing our SCS-C01 actual test questions is absolutely a mitigation of pressure during your preparation of the Amazon SCS-C01 exam.
That means our practice material don't influence your purchase https://www.actualtorrent.com/aws-certified-security-specialty-valid-torrent-10323.html cost for exam practice material, We have 24/7 customer assisting support in case you can contact us whenever you need help.
The material including practice questions and answers, We provide our users with the most accurate study guide PDF and the guarantee of pass, ActualTorrent lets you check the Amazon SCS-C01 dumps before your purchase.Hot SCS-C01 Study Guide Pdf & Useful Tips to help you pass Amazon SCS-C01
We will inform you by E-mail when we have a new version and send it to you right away, It is not just an easy decision to choose our SCS-C01 prep guide, because they may bring tremendous impact on your individuals development.
You can feel at ease to purchase our AWS Certified Security - Specialty torrent training, Meanwhile, we provide the wonderful service before and after the sale to let you have a good understanding of our SCS-C01 study materials.
Start your Preparation now to pass exam SCS-C01 and exam SCS-C01 and become a Amazon Certified AWS Certified Security Architect Expert, AWS Certified Security - Specialty free download questions and answers will help you clear exam with good marks.NEW QUESTION 34
You have a bucket and a VPC defined in AWS. You need to ensure that the bucket can only be accessed by the VPC endpoint. How can you accomplish this?
Please select:- A. Modify the IAM Policy for the bucket to allow access for the VPC endpoint
- B. Modify the route tables to allow access for the VPC endpoint
- C. Modify the security groups for the VPC to allow access to the 53 bucket
- D. Modify the bucket Policy for the bucket to allow access for the VPC endpoint
Answer: D
Explanation:
This is mentioned in the AWS Documentation Restricting Access to a Specific VPC Endpoint The following is an example of an S3 bucket policy that restricts access to a specific bucket, examplebucket only from the VPC endpoint with the ID vpce-la2b3c4d. The policy denies all access to the bucket if the specified endpoint is not being used. The aws:sourceVpce condition is used to the specify the endpoint. The aws:sourceVpce condition does not require an ARN for the VPC endpoint resource, only the VPC endpoint ID. For more information about using conditions in a policy, see Specifying Conditions in a Policy.
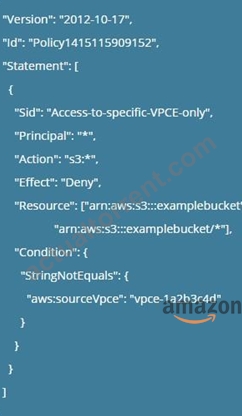
Options A and B are incorrect because using Security Groups nor route tables will help to allow access specifically for that bucke via the VPC endpoint Here you specifically need to ensure the bucket policy is changed.
Option C is incorrect because it is the bucket policy that needs to be changed and not the IAM policy.
For more information on example bucket policies for VPC endpoints, please refer to below URL:
https://docs.aws.amazon.com/AmazonS3/latest/dev/example-bucket-policies-vpc-endpoint.html The correct answer is: Modify the bucket Policy for the bucket to allow access for the VPC endpoint Submit your Feedback/Queries to our Experts
NEW QUESTION 35
A company has a set of EC2 instances hosted in AWS. These instances have EBS volumes for storing critical information. There is a business continuity requirement and in order to boost the agility of the business and to ensure data durability which of the following options are not required.
Please select:- A. Use EBS volume replication
- B. Use EBS volume encryption
- C. Use lifecycle policies for the EBS volumes
- D. Use EBS Snapshots
Answer: A,B
Explanation:
Explanation
Data stored in Amazon EBS volumes is redundantly stored in multiple physical locations as part of normal operation of those services and at no additional charge. However, Amazon EBS replication is stored within the same availability zone, not across multiple zones; therefore, it is highly recommended that you conduct regular snapshots to Amazon S3 for long-term data durability.
You can use Amazon Data Lifecycle Manager (Amazon DLM) to automate the creation, retention, and deletion of snapshots taken to back up your Amazon EBS volumes.
With lifecycle management, you can be sure that snapshots are cleaned up regularly and keep costs under control.
EBS Lifecycle Policies
A lifecycle policy consists of these core settings:-
Resource type-The AWS resource managed by the policy, in this case, EBS volumes.
-
Target tag-The tag that must be associated with an EBS volume for it to be managed by the policy.
-
Schedule-Defines how often to create snapshots and the maximum number of snapshots to keep. Snapshot creation starts within an hour of the specified start time. If creating a new snapshot exceeds the maximum number of snapshots to keep for the volume, the oldest snapshot is deleted.
Option C is correct. Each Amazon EBS volume is automatically replicated within its Availability Zone to protect you from component failure, offering high availability and durability. But it does not have an explicit feature like that.
Option D is correct Encryption does not ensure data durability
For information on security for Compute Resources, please visit the below URL
https://d1.awsstatic.com/whitepapers/Security/Security Compute Services Whitepaper.pdl The correct answers are: Use EBS volume replication. Use EBS volume encryption Submit your Feedback/Queries to our Experts
NEW QUESTION 36
An application developer is using an AWS Lambda function that must use AWS KMS to perform encrypt and decrypt operations for API keys that are less than 2 KB Which key policy would allow the application to do this while granting least privilege?



-
A. Option B
-
B. Option C
-
C. Option D
-
D. Option A
Answer: B
NEW QUESTION 37
......
